
Enhancing Readiness for National Cyber Defense through Operational Collaboration
The 2020 New York Cyber Task Force Report
Enhancing Readiness for National Cyber Defense through Operational Collaboration
The New York Cyber Task Force, gathered for the second time to build upon the accomplishments of the 2017 task force, addressing how the US government and private sector can enhance cyber readiness through operational collaboration to protect the nation. The group, co-chaired by Greg Rattray (Next Peak), Evan Wolf (Crowell & Moring), and Merit Janow (Columbia University SIPA) has synthesized efficient recommendations seeking to create an effective, whole-of-nation approach to enable enhanced cyber readiness through operational collaboration. At their core, these recommendations focus on establishing a public-private network of empowered nodes to provide effective crisis response to strategic cyber contingencies.
Strengthening national cyber readiness should be seen as an opportunity, not as a burden. Cyber readiness in the face of severe but plausible cyber shocks will enable confidence in the digital transformations already underway. The campaign to defeat the coronavirus has taught us lessons about the need for resiliency, the need for collaboration across all levels of government and with the private sector, and the fundamental role trust plays in achieving such collaboration. The United States does not have to wait to learn these lessons over again if an adversary inflicts a severe cyber crisis upon us. The nation must get ready now.
Report Excerpts
The United States must reduce its vulnerability to strategic disruption by adversaries acting through cyberspace. Geopolitical and social forces, growing technological dependencies, and inherent advantages for ever more capable cyberattackers raise the risk of a major cyber crisis. Such a crisis could have significant adverse effects on public health and safety, the economy, and national security. Given mounting cyber challenges, the United States must take immediate steps to improve its cyber readiness to withstand such potential attacks.
In the spring of 2020, the School of International and Public Affairs (SIPA) reconvened the New York Cyber Task Force (NYCTF) to develop approaches to enhance cyber readiness through public-private operational collaboration that would enable more effective coordinated responses to cyber crises. The NYCTF assessed future risks to U.S. national security stemming from cyber challenges including political, economic, and technological developments; changing cyber conflict dynamics; and the COVID-19 pandemic. We then envisioned severe, yet plausible, scenarios projected for 2025 to examine how well the nation could defend itself in cyberspace. By looking to the future, the NYCTF shifted away from yesterday’s issues to focus on longer-term enhanced cyber readiness. Our deliberations consistently identified shortfalls in our current operational collaboration capabilities and effective coordination efforts.
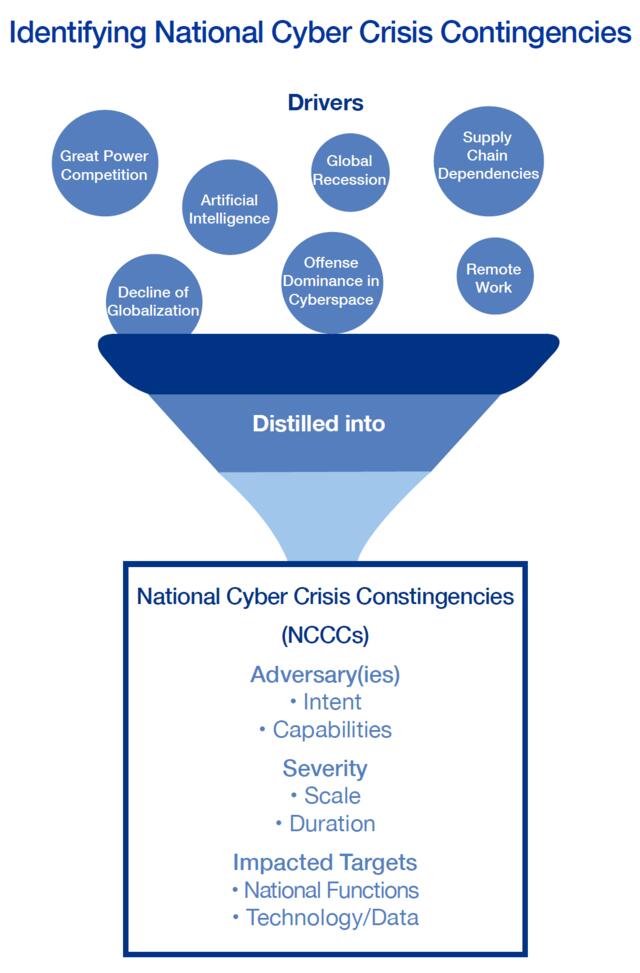
Our first step was identifying drivers of cyber challenges that may exist in 2025. Seven categories were examined: global politics, U.S. domestic politics, economic, technology, cyber ecosystem instability, systemic cyberattack advantages, and systemic cyber defense weaknesses. As COVID-19 took hold, an eighth category was identified to reflect the societal and technological challenges presented by the pandemic. The Task Force identified many challenges to operational collaboration, the most pressing of which stemmed from a lack of established, exercised, and effective organizations to integrate public and private sector cybersecurity planning and response capabilities in a time of crisis.
Next, the Task Force designed a set of four scenarios that present a series of severe but plausible challenges to national security. These scenarios covered a range of adversaries, potential attack vectors, and geo-political, economic, and technological factors that could combine to create very stressful cyber crises that might arise in 2025. This exercise was not an attempt to predict the future. However, the NYCTF leveraged deep expertise in considering the nature of scenarios worth further deliberation. Opinion can and will vary regarding the degree to which different drivers might come together and create a potentially severe cyber crisis. A multiplicity of potential toxic brews exists. The NYCTF believes that these scenarios serve as strong starting points to illuminate reasonable planning contingencies. We established the following four scenarios:
- Scenario 1: Rising tensions in the Middle East lead to an increased U.S. presence in the region supporting Saudi Arabia and alarming Iran. The rapid integration of smart technology in U.S. critical infrastructure creates exploitable vulnerabilities. Iran uses these vulnerabilities to coerce the U.S. by targeting major metropolitan areas with disruptive attacks against the electrical and transportation sectors, causing intermittent power outages.
- Scenario 2: China continues its rise as a competitive global player. China’s rise as a global tech competitor enabled penetration of Internet of Things (IoT) devices and Artificial Intelligence (AI) databases, enabling for IoT- and AI based attacks on U.S. infrastructure in under-regulated critical industries. As tensions mount in the APAC region, China mounts a major disruptive attack against logistics, shipping, and healthcare, limiting the ability to marshal a response.
- Scenario 3: North Korea, seeking to launder funds to enable nuclear weapons development, leans on cryptocurrency and cybercrime to funnel funds. As the digital underground thrives with North Korean sponsorship, criminal capabilities rapidly evolve. When tensions on the Korean peninsula eventually erupt, North Korea uses advanced cloud exploits to penetrate the financial system and wipe data, disrupting financial services. Attacks are amplified by cybercriminal actors using North Korean provided tools.
- Scenario 4: As wealth disparities increase, driven by ever larger technology conglomorates, the nation moves to cloudbased, IoT-driven smart cities. Domestic political events and declining levels of public trust give rise to domestic extremist groups motivated by growing wealth divides. As public opinion drops to an all-time low, domestic extremist groups exploit the growth in IoT devices to launch amplified DDoS attacks, disrupting smart technology dependent emergency services and the media, causing disrupted responses and jammed lines of communication, while exasperating civil unrest with divisive messaging.
Effective national cyber crisis response requires a wide range of organizations to conduct complex technical and operational activities rapidly and in synchronized fashion across a variety of geographies and technical systems. Because the public and private sectors each have distinct comparative advantages in cyberspace, effective cyber crisis response will require both sectors to provide their unique capabilities. Thus, the nation’s cyber readiness depends on the coordination of capabilities across the full spectrum of organizations at all levels of government and the private sector.
Recommendation 1: Identify National Cyber Crisis Contingencies
To assess our readiness, identify deficiencies, and recommend improvements, our nation must identify the key national security challenges that will confront our collaborative cyber defense effort. The NYCTF recommends that the Office of the National Cyber Director work with all stakeholders at Federal, state, and local levels and including the private sector to establish a program to identify a prioritized set of national cyber crisis contingencies (NCCCs) to:
- Guide selection of the organizations, communications, and responsibilities within the National Cyber Response Network (NCRN)
- Establish criteria for situational awareness by the NCRN in event of these NCCCs, based on potential impacts and risks, including the effect of an attack’s scale, duration, and severity
- Focus of planning and exercise activities by the NCRN and the associated NCRN nodes leveraging public and private sources of information regarding adversary intentions and capabilities
- Provide criteria for assessing the readiness of the NCRN
- Establish a program to ensure the NCCCs are up to date and that findings from assessments are used to drive operational and budgeting priorities
- Provide the basis for exercises of the NCRN

Recommendation 2: Establish a National Cyber Response Network
Our nation should approach cyber readiness through establishing a collaborative, coherent network leveraging existing information sharing and analysis organizations (ISAOs), network operations centers (NOCs), and cyber response teams in the government and the private sector, especially those response responsibilities for national critical functions. The NYCTF recommends the new National Cyber Director designate a Federal government agency to lead a national effort to establish a National Cyber Response Network (NCRN).
- The NCRN organizations would connect a wide range of existing and potentially new organizations across all levels of government and in collaboration with the private sector.
- The NCRN organizations must be empowered in advance to orchestrate specific response actions for cyber defense during severe cyberattacks.
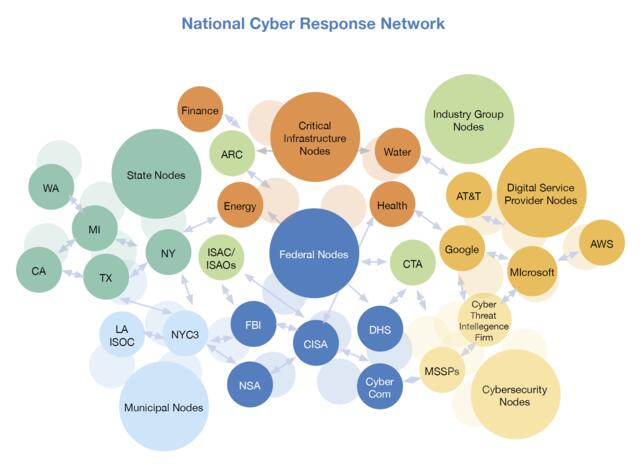
Recommendation 3: Operation of the NCRN
To leverage a collaborative NCRN, our nation must establish the capability to coordinate activity and share situational awareness among key governmental and private sector players engaged in national-level cyber crisis response.
- The federal lead agency would conduct overall coordination and enable readiness of designated NCRN nodes.
- The federal lead agency would establish a common concept of operations for the NCRN in consultation with operators of the designated NCRN nodes.
- The federal lead agency would enable situational awareness across the NCRN through establishment of a common operating picture for use during National Cyber Crisis Contingencies (NCCCs). The common operating picture must be developed in consultation with operators of the designated NCRN nodes.
- Designated NCRN nodes would use the common concept of operations. These nodes would be responsible for developing the required integrative capabilities to leverage the common operating picture and participate in exercise and training to ensure readiness.
Recommendation 4: Assess National Cyber Response Capabilities to Ensure Readiness
The NYCTF believes the United States is insufficiently prepared for the types of contingencies considered in the scenarios. Assessing the readiness of U.S. cyber response capabilities is essential to guiding actions and investment. Assessment efforts should recognize both the challenges and the opportunities that stem from the distributed nature of U.S. capabilities that reside in many organizations in the private and public sectors. The NYCTF recommends the ONCD should be responsible for establishing a national cyber readiness framework in collaboration with the participants in the NCRN. The NCRN will clearly outline the nature of cyber response capabilities necessary to respond effectively to the NCCCs, seeking to establish minimum requirements and identify capacity gaps across private and public stakeholders. The federal lead agency for the NCRN should use this framework to conduct annual assessments in conjunction with the designated nodes to assess readiness for the identified NCCCs. This cyber readiness framework should:
- Set standardized definitions for capabilities and resources
- Establish minimum readiness and capacity requirements for response to identified NCCCs
- Enable shared understanding of necessary capabilities, facilitating investment decisions and expectations of deployment of key HV/LD capabilities across public and private sectors
- Direct ongoing capability and gap assessments for all participants in light of the NCCCs identified by the ONCD
Recommendation 5: Ensure National Cyber Readiness through Training and Exercises
The United States needs to ensure the availability of the right skilled personnel and exercise its ability to respond to NCCCs in a vigorous, structured fashion to understand our readiness and potential weaknesses. The designated federal lead agency for the NCRN should cooperate with participants in the network to establish ongoing public-private training and exercise programs that will build proficiency in managing cyber crisis response operations. Exercises should be mapped to the NCCCs. The assigned federal lead agency should:
- Coordinate with NCRN participants in the conduct of an ongoing collaborative training and exercises program linked to key National Cyber Crisis Contingencies (NCCCs)
- Establish playbooks in consultation with the NCRN participants for national crisis response focused on the key NCCCs
- Over time, establish a national cyber training and exercise range to ensure command, control, and communications systems are adequately tested and functional in the case of a cyber crisis
During our deliberations, NYCTF members devoted significant time to discussing barriers that might impede effective operational collaboration. In many cases, challenges to achieving deeper operational collaboration have existed for an extended period such as establishing integrated information sharing to empower cyber incident response, legal and procedural barriers to sharing information, and mobilizing response resources as well as limited human and financial resources available to proactively enhance cyber response capabilities. In other situations, the NYCTF identified emerging challenges that may impede future operational collaboration including how new technologies may pose emerging vulnerabilities and risks as well as factors in our society between institutions.. Here the Task Force identifies five enabling recommendations that the NYCTF believes will have the greatest positive impact.
Enabling Recommendation 1: Establish Integrated Cyber Crisis Information Networks
The United States must work to ensure that cyber responders can leverage a robust range of information and knowledge across the diverse ecosystem of organizations and perspectives that will make up the NCRN. The designated federal lead agency leading the National Cyber
Response Network (NCRN) should collaborate with operators of the designated nodes to establish national integrated information streams orchestrated to collect and disseminate key information between NCRN organizations to better prepare and respond.
Enabling Recommendation 2: Address Technology Evolution to Ensure Readiness
The NYCTF analysis of drivers for national security emerging for the U.S. in cyberspace continuously returned to the challenge of the speed of technology changes, complexities such change causes for seeking collaboration, and coordination in response to cyberattacks. The NYCTF recommends national efforts should seek to engage and enable leading private sector technology firms and organizations, in addition to private-held national critical functions providers, in cloud computing services, Internet of Things (IoT), and artificial intelligence (AI) to develop the capabilities to engage in the establishment of the NCCs and participate in the National Cyber Response Network (NCRN).
Enabling Recommendation 3: Remove Legal and Procedural Barriers to Enhance Response
The NYCTF found that despite ongoing attention in past studies regarding how existing laws, regulation, and proscribed processes negatively impact private-public operational collaboration, these barriers remain high. Additionally, the lack of clarity of existing laws, regulation, and procedure can paralyze action in the case of a cyber crisis. The nation needs to continue proactively clarifying authorities and establish appropriate agreements to remove legal concerns hindering effective public-private response in times of crisis.
Enabling Recommendation 4: Build Trust and Confidence for Cyber Crisis Response
In order to effectively collaborate in cyber response, a wide range of organizations will need to trust each other and the information streams and situational awareness they will share. The nation needs to establish widely accepted trusted sources of information and analysis regarding cyberattacks, the attackers, and the impacts on targeted organizations, sectors, and society, within public-private operational constructs. Specific steps recommended by the NYCTF include:
- Encourage and enable the private sector and different levels of government to have liaisons, secondments, and alternative programs to exchange personnel to improve collaboration processes and build trust between organizations
- Encourage cybersecurity officials to cultivate relationships with traditional media organizations and reporters to build trust, and ensure that accurate, substantive feeds of relevant information have a channel to the public domain
- Co-design, with public and private stakeholders, improved digital literacy programming to educate on understanding what constitutes misinformation during a cyber crisis, how to distinguish factual reporting from disinformation related to cyber events, and how to report misinformation to help enable platform managers to take down inappropriate content
- In moments of cyber crisis ripe for disinformation campaigns, ensure that the government and media companies have appropriate active collaborative mechanisms to moderate content with stricter fact-checking, publishing criteria, and warnings of misinformation campaigns when they occur
Enabling Recommendation 5: Close Resource Gaps to Ensure Readiness
The nation must invest deeply if the capabilities outlined above are to exist. These investments should come from both public and private sectors. The U.S. government should work to establish a well-funded national program for enhanced cyber response capabilities across all levels of government and the private sector. This program must be considered a national defense priority.
New York Cyber Task Force Reports
The New York Cyber Task Force has spent the last year investigating the private sector’s perspective on the current and future state of operational collaboration, as well as to understand the federal government’s aims and aspirations in improving how industry and government work together.
The New York Cyber Task Force report released a series of recommendations that would help make it easier to defend cyberspace without sacrificing the utility, flexibility, and convenience that has made the Internet so essential to our economies and personal lives.

